QueryPie Overview
This article pertains to QueryPie Enterprise version 9.16.0.
QueryPie: Your Cloud Data Protection Platform
As privacy regulations continue to evolve, many organizations are recognizing the importance of implementing robust security management solutions to comply with these regulations. QueryPie stands out as a cloud-optimized data governance platform offering cutting-edge solutions for data security in the modern cloud environment. It encompasses features such as database and system access control, audit logs, Privacy Discovery, Kubernetes integration, and more.
Beyond merely addressing security concerns, QueryPie offers a comprehensive solution for managing IT assets effectively. Whether it's databases, systems, or containers, QueryPie provides a unified data environment aimed at streamlining asset management and fostering collaboration among teams. With QueryPie, users can centralize complex access management tasks, effortlessly grant or restrict permissions, and maintain precise control over their IT assets.
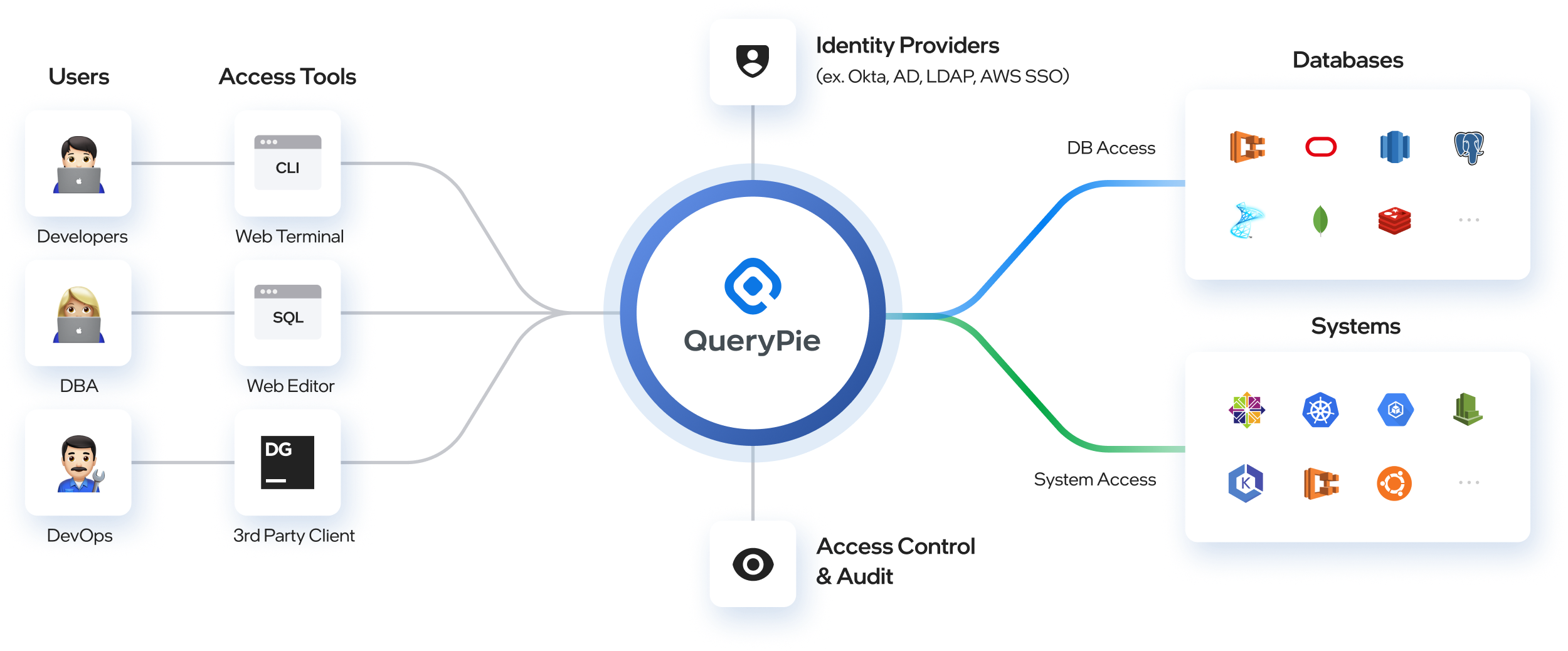
How QueryPie Works
QueryPie key features
Granular access control: Manage user access at various levels, including network, tables, columns, and system protocols, ensuring access is tailored to specific tasks.
Unified interface: Access and manage multiple databases and system platforms via a single, intuitive web browser interface. QueryPie seamlessly integrates with various cloud providers for simplified resource management.
Real-time monitoring: Monitor user activity in real time with comprehensive auditing features. Detect abnormal access attempts, unauthorized queries, data changes, and potential security breaches to maintain a strong security posture.
Workflow integration: Streamline access requests and approvals with automated workflow capabilities. Automate access requests, query executions, and other collaborative tasks requiring approvals and audits.
Data masking: Protect sensitive data with customizable data masking policies. Enforce additional authentication for authorized users or exceptions for sensitive information.
Compliance: Ensure compliance with domestic and international regulations. Extract audit logs for authentication and auditing purposes, maintaining regulatory adherence.
Manual Guideline
At QueryPie, our continuous focus revolves around enhancing the protection of your organization's sensitive data in the cloud. Currently, QueryPie offers fundamental features such as database and system access control, along with auditing capabilities. This documentation serves as a comprehensive guide, empowering security personnel to establish and maintain robust access control and auditing functionalities within their organizations using QueryPie. From the initial system setup to resource registration, policy configuration, and audit log monitoring, this guide aims to provide step-by-step instructions for leveraging QueryPie effectively.
Below are the links to assist you in quickly accessing the information you may require:
Access to the QueryPie Quick Guide
Administrator
User Management
DB/Server Management
DB Registration
Server Registration
Policy Management
Manage DB Policies
Manage Server Policies
Workflow Management
Security Management
User
Approval Request
Connection to Resources
%201.png)