Set Up Server Access Policies
Overview
You can manage and enforce access policies for each server or group of servers your organization oversees. This includes setting specific days and times for access, identifying multiple failed attempts within a defined timeframe as an anomaly, and subsequently blocking the account from accessing the server. Additionally, you can stipulate the maximum number of sessions allowed per user, restrict commands, and more.
Set Up Server Access Policies
Server access policies can be set on servers and server groups.
Settings > Server Settings > Connection Management > Servers
Settings > Server Settings > Connection Management > Server Groups
If the server is included in a server group, it automatically inherits the policies set for that group. However, if the server's policy inheritance setting is configured to "Operate separately," it will have its own independent set of policies without inheriting those of the server group.
Server Settings > Connection Management > Servers or Server Groups
Navigate to Server Settings > Connection Management > Servers or Server Groups menu.
Select the desired server or server group from the list.
Scroll down to the Policy section located at the bottom.
For each item, input the following details to configure the policy:
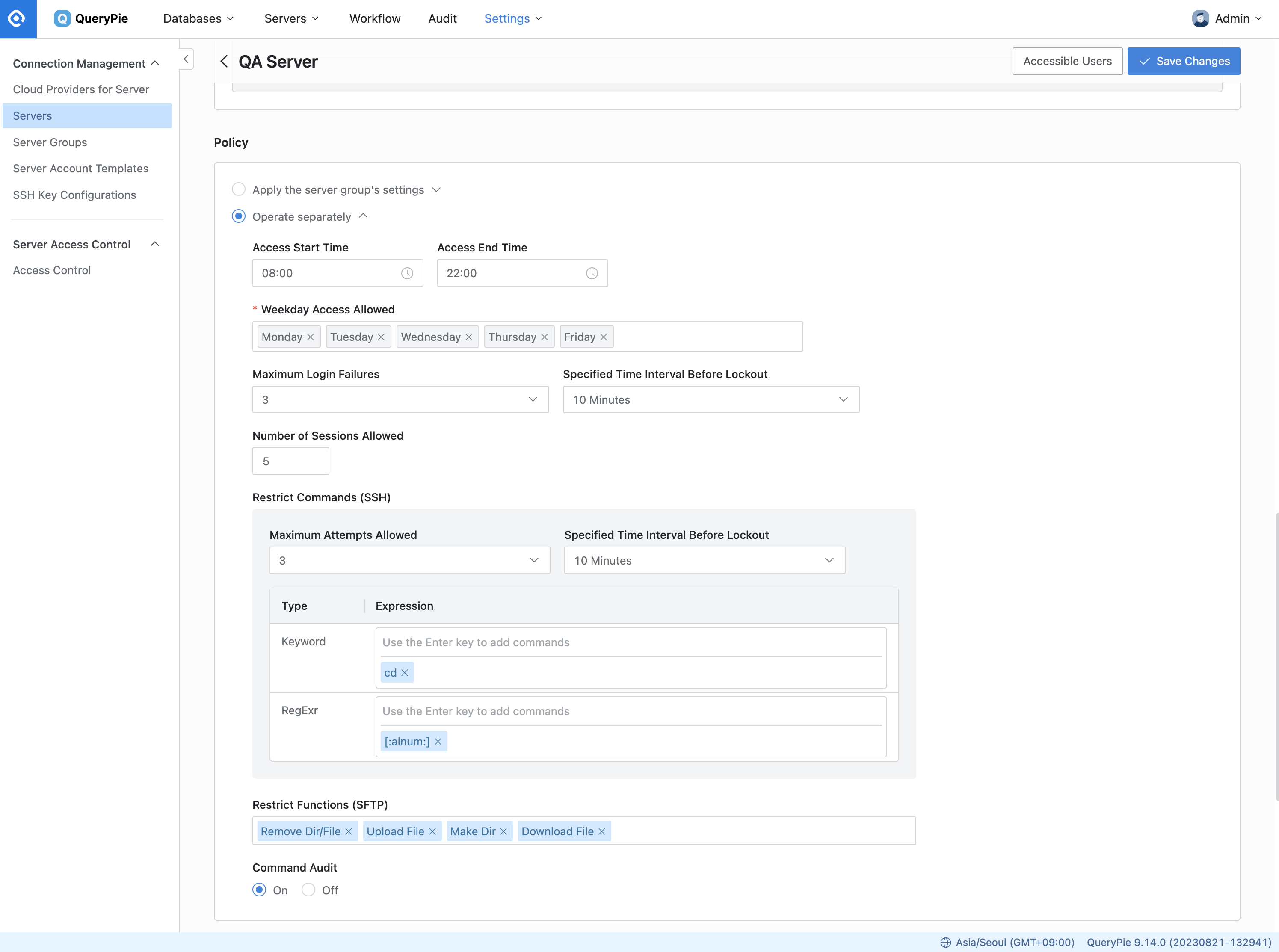
Access Start Time : Specify the start time for the connection's accessibility in the designated time zone.
Access End Time : Specify the end time for the connection's accessibility in the designated time zone.
Weekday Access Allowed : Choose the days of the week when the connection is accessible.
Maximum Login Failures: Define the maximum number of login failures permitted for this connection.
Specified Time Interval Before Lockout: Set the time interval within which the maximum login failures are counted.
For instance, suppose you configure the maximum number of failed login attempts to be 3 within a time frame of 10 minutes.
In this scenario, if a user experiences 3 failed login attempts within the specified 10-minute window, it will trigger a policy violation, resulting in the account being locked out.
Consequently, the affected account will no longer be able to access the server using those credentials.
Number of Sessions Allowed: Determine the maximum number of sessions allowed per user on the server. The default value is 1, and you can enter up to 9,999.
Restrict Commands (SSH): Define policies for commands executed via the web terminal on the server.
Maximum Attempts Allowed: Limit the number of times a prohibited command can be executed.
Specified Time interval Before Lockout: Set the time interval for counting prohibited command executions.
Keyword : Specify the banned command as a keyword.
RegExr: Specify the banned command as a regular expression.
Restrict Commands (SFTP): Set policies for actions performed over web SFTP. You have the option to limit various actions such as directory/file deletion, file upload, file download, and directory creation.
Command Audit: Choose whether to log executed commands on this server (Default = On).
Once you have configured the policies, click the
Save Changesbutton at the top right corner to apply the settings.
%201.png)